In George Orwell’s classic novel 1984, he painted a distinct and vivid picture of a dystopian world with little privacy or freedom of expression. While it was a work of fiction, it is becoming more real by the day and this is why secure communication tools are needed in the modern world. It is also why we, the 1984 Group, have developed a system such as Utopia that has been needed for a long time now.
One of the biggest guiding principles of Utopia is that it is a peer-to-peer network and more specifically, a third-generation peer-to-peer network. Peer-to-peer networks are important because they bypass the centralized system typically used which relies on a central server.
The reason that central servers have to be bypassed is that the entire digital architecture depends on that central server to perform efficiently for all users to access services. This means that the servers are hugely vulnerable to hacks, breakdowns, and other issues. If they fail, the entire system fails, and given that the servers are run by people, vulnerability is always an issue. This is why we have chosen to reject centralized servers and offer a system of full confidentiality and anonymity through which all nodes connected to the network are equal.
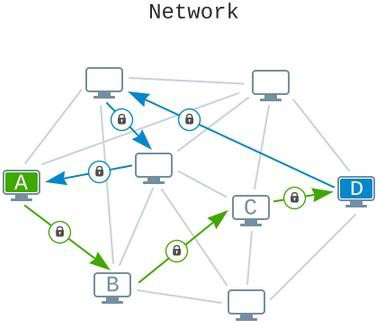
One issue that usually occurs in the organization of a censorship-resistant network is connecting to other P2P network nodes. A number of platforms opt to use a central server to get around this problem but they often constitute a weakness over time.
That is why we are choosing not to use a centralized server and instead, we are solving the issue of primary node searching with a number of creative methods. The Utopia network has a node search cascade algorithm through which users can access the network without any issue of censorship at any level. While a number of factors such as that user’s type of network connection and the level of censorship in their specific region might play a part, Utopia’s software will use a number of ways to search for the initial peers:
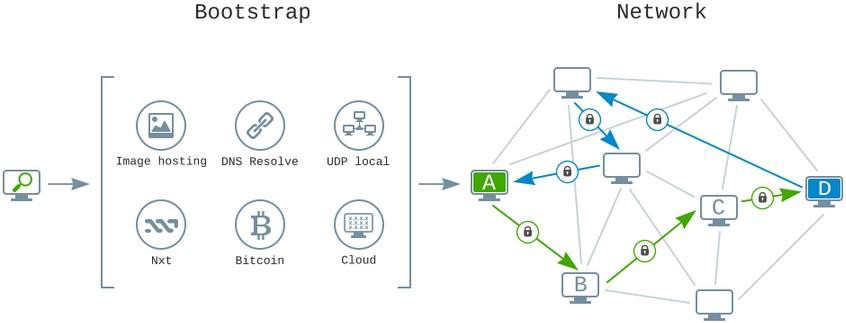
First and foremost, Utopia will attempt to retrieve a list of possible peers from pre-defined IP addresses in the distribution through IP/DNS Resolve. If censorship prevents Utopia from accessing the IP address data, it moves on to the UDP local technique. The broadcast of requests to connect to local subnet nodes in particular.
If that doesn’t succeed, a scan will take place of the Internet by the Utopia client for replaced images that have the IP address of their initial peers encrypted. This means that no one will be able to stop the posting of pictures on the Internet. But this is not the only method we have at our disposal. The network will also search for bitcoin transactions and this is because the initial IP addresses of the peers are encoded in the transaction amounts.
NXT, another crypto, will also go through the same process. There are other additional methods that will not be publicly disclosed to avoid exploitation but be rest assured that those will help in the P2P connection process on the Utopia network. But we will need some help from our users as staying online for as long as possible will help the network to function better and be more reliable for you.
We understand that there will be some curiosity about the security of our transmission process and this is something we take very seriously. Two layers of modern elliptical restriction will be used before messages are transmitted across the network and public information about that can be found here.
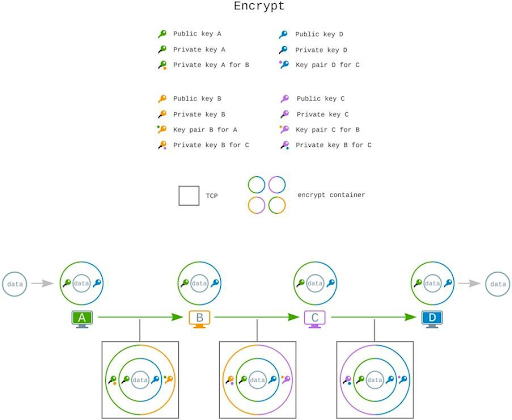
The algorithm for encryption we use is non-compromised, modern, and uses an open-source cryptographic library. All data is encrypted using a keypad that both the sender and the recipient have access to but our encryption process is not limited only to this.
During the process of peer-to-peer encryption, a second layer using a temporary private and public key can be used for additional encryption. This double layer of encryption means that your data is saved from everyone who might want to access it. There is also packaging using the TCP transport protocol which means the pockets of transmitted information are hidden under frequently used data protocol. This means that even your Internet service provider cannot detect traffic from Utopia and this gives an unparalleled level of security and anonymity for users.
We’re also happy to announce that we’ve developed a routing algorithm that is based on the calculation of the optimal message delivery path. The goal of this algorithm is to remove certain disadvantages of DHT routing like database weights. The algorithm also bypasses some of the downsides of broadcast and does not clog the communications channels with huge loads. Compared to modern missiles that can change the direction mid-flight to reach their targets, the data packets in our network and also change the transmission pathways to make sure confidentiality and privacy are maintained.
Decoy TCP packets are also sent periodically to mislead any technical means of analysis and make sure that the deanonymization of users of the network is impossible.
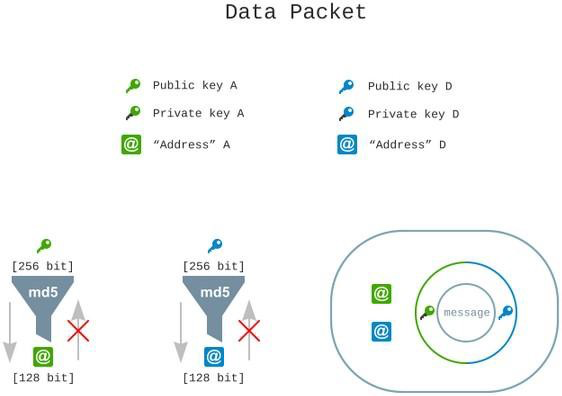
When forwarding messages, it’s worth rethinking the idea of scoring routing. For each element of the set of open network connections, each intermediary (transit) node of the network performs the operation of accumulating statistics of messages traveling through it. The accumulation occurs as nodes that are assured to perform network activity at the senders’ addresses (in the set of 128 bits).
The node then evaluates if this network connection is adequate for delivering the message down the final path based on these statistics. The rating is based on how frequently and successfully the communication channel has been utilized to send or transmit data between nodes.
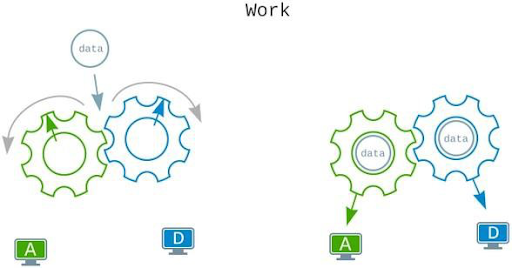
When a message is forwarded, one of the complicated mechanism’s gears spins, delivering the next encrypted message’s delivery directions. Based on the transfer data made by other nodes, the ideal direction can be established at each moment of time. For improved anonymization of network users, the route changes somewhat from the previous one at the next point in time.
All nodes in the network are cogs in huge machinery with one objective in mind: to keep the network running while also supporting user security and anonymity.
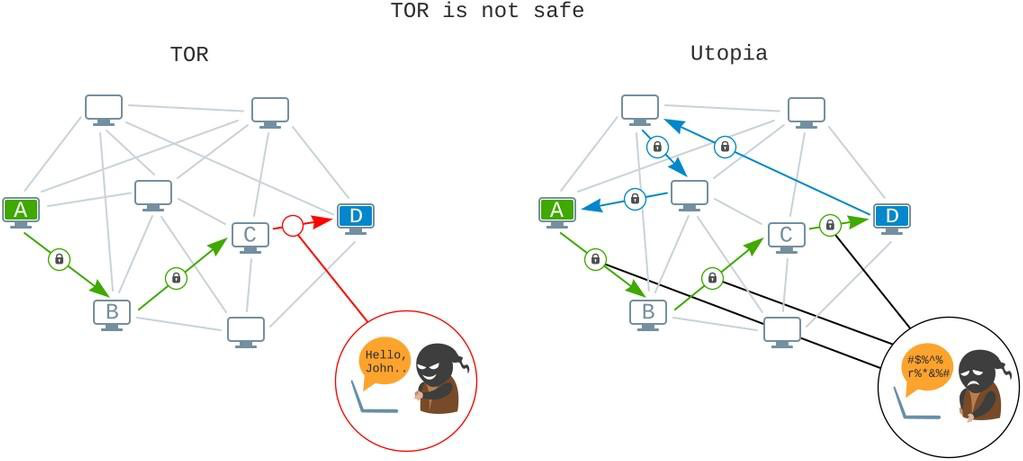
The reader’s thoughts might naturally jump to a comparison with the Tor network. Rumors about its total security are vastly overblown, as evidenced by several incidents of the genuine owners of Tor resources being deanonymized. It is impossible to ensure sufficiently secure data transit and user anonymity if no encryption is used when connecting to the input and output nodes.
The user’s true IP address is known by the input node, and the outgoing node can accumulate all data except this IP node. Regardless of the mode of operation selected, a considerable amount of data can be made available to other persons and organizations: your trips to various websites, your usernames and passwords, any personal confidential data, and, eventually, your true IP address.
Furthermore, any traffic analysis tool may detect Tor usage, thus your internet provider is aware of your Tor usage. This means that, at the request of state agencies, the provider can pass up all details, including who did what, when, and with what device and network address, as well as whether or not the TOR network was used. Do you think Tor is still safe to use? Probably not.
To summarise the Utopia network’s operating principles, we’d like to point out that it’s a peer-to-peer decentralized self-regulating ecosystem. To work indefinitely, the Utopia network requires only users (nodes). With more users, the network becomes more stable and secure.
Within the network, all data is only sent in a double-encrypted format. Private messages are symmetrically encrypted twice, while channel messages are symmetrically encrypted twice (this makes it possible to decrypt a message from any channel participant rather than a predefined user with a given key).
Any device on the Utopia network works to anonymize message senders/recipients and, of course, to assist in determining the most efficient route of transmitted data. The content of the sent data is only known by the sender and recipient due to the implementation of various levels of encryption.
Even metadata is missing from transmitted data, making even indirect information about network customers impossible to collect. Temporary keys, which support the upper level of encryption, as well as hashing the sender and destination addresses, are used to anonymize network nodes.
Your internet service provider won’t be able to tell the difference between encrypted Utopia traffic and VOIP phone calls or online video because the network packets are masked.

